COMS W4118 Operating Systems I
System Calls
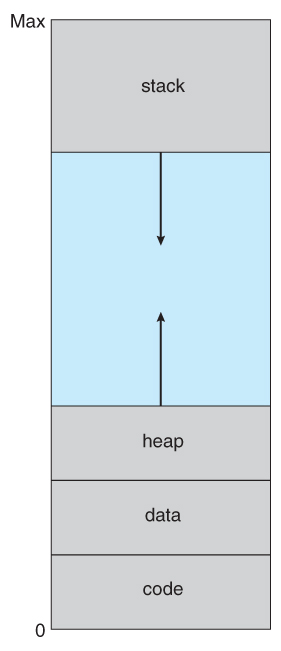
Virtual Address Space Revisited
Recall strace: shows syscalls invoked during program execution.
Heap
malloc() does not appear in the strace, because it is not a syscall. How does
process increase the size of its heap?
See the following lines in strace output:
brk(NULL) = 0x558d52610000
brk(0x558d52631000) = 0x558d52631000
brk(): changes the location of the program break, which defines the end of the
process’s data segment (i.e., the program break is the first location after the
end of the uninitialized data segment). Increasing the program break has the
effect of allocating memory to the process; decreasing the break deallocates
memory.
A program’s break is the address of the top of its heap. brk(NULL) gets the
current process break and break(addr) sets the break to addr.
File-backed mappings
Program setup involves mapping in the C standard library:
openat(AT_FDCWD, "/lib/x86_64-linux-gnu/libc.so.6", O_RDONLY|O_CLOEXEC) = 3
mmap(0x7f6e911ec000, 24576, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x1e7000) = 0x7f6e911ec000
close(3)
Recall from L05-ipc: use mmap() to create a file-backed mapping in virtual
memory:
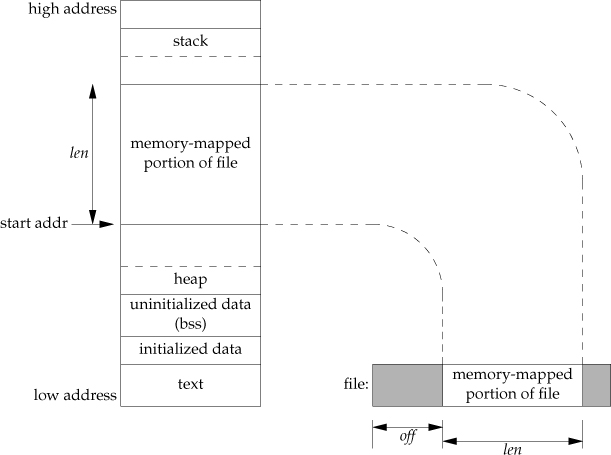
Region of virtual memory refers to a “snapshot” of the file in memory, i.e. a “page”.
Full Reveal: Virtual Address Space
All regions of virtual memory map to a page of physical memory:
- indirect mapping: requires OS/hardware to perform translation
- direct mapping: linear mapping between virtual and physical memory
All processes have a direct mapping to shared kernel code & data
- e.g.
task_structlists, per-process kernel stack, file sharing data structures are stored here
Kernel mapping is above the stack, but is not accessible to userspace program because of memory protection. How do syscalls safely access kernel mapping?
Processor Modes
CPU runs with a privilege mode that determines what kind of operations it can perform:
- User mode: cannot perform privileged operations or directly access hardware
- Kernel mode: can perform privileged operations and has full access to hardware
A userspace program (running in user mode) can issue a syscall (e.g. read())
to enter kernel mode so that it can perform a privileged operation (e.g. issue
I/O request).
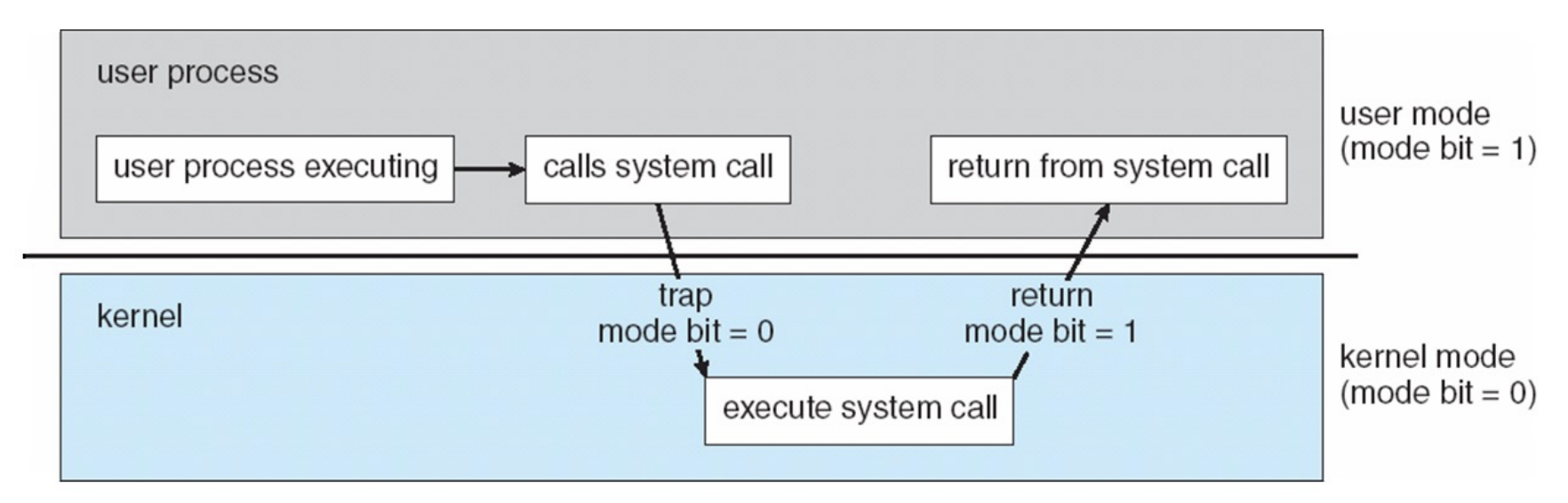
Syscalls act as predefined entry-points into the kernel. They allow userspace programs to “trap” into the kernel to perform a privileged operation and then “return-from-trap” back to user mode.
Interrupts
Need some sort of indicator to tell the processor to stop executing user code and trap into the kernel to perform privileged operations.
Three kinds of interrupts:
- Hardware interrupts
- asynchronous
- e.g. network packet arrival, timer, key press, mouse click
- Exceptions/Faults
- synchronous
- e.g. dividing by zero, page fault
- Software interrupts
- synchronous
- x86 assembly
int: raise software interrupt - e.g. syscall (
int 0x80), debugger
Simplified CPU hardware execution loop:
while (1) {
if (interrupt or exception) {
n = interrupt/exception type
call interrupt handler n
}
fetch next instruction
if (instruction == int n)
call interrupt handler n
else
run instruction
}
Note: do not confuse interrupts with userspace signals!
- Signals: enables communication between processes and OS
- Interrupts: enables communication between hardware and OS
- but some interrupts can generate userspace signals…
- divide by zero exception:
SIGFPE - illegal memory access:
SIGSEGV
- divide by zero exception:
- but some interrupts can generate userspace signals…
Linux System Call Dispatch
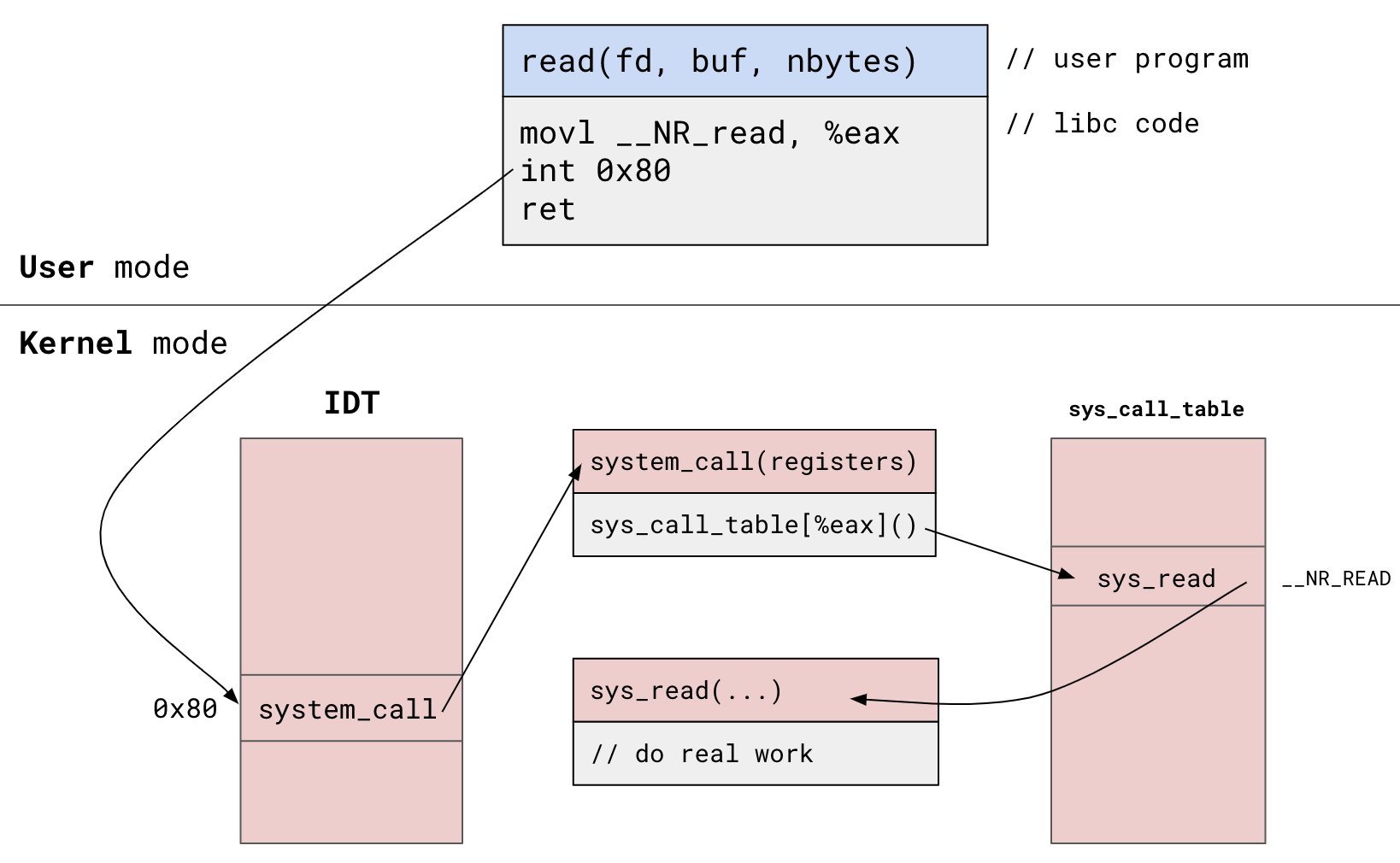
User program invokes read():
- libc system call wrapper invokes software interrupt
0x80(system call)- Places syscall number
__NR_readinto%eaxregister
- Places syscall number
- Trap into kernel mode, look up
0x80in Interrupt Descriptor Table (IDT) - Jump to interrupt
0x80’s handler:system_call() system_call()looks up__NR_readinsys_call_table- Unpack registers, call
__NR_read’s handler:sys_read() - Perform
read()’s real work insys_read()- file entry management, I/O requests, copying data, etc.
Notes:
int 0x80is how syscalls were invoked in 32-bit x86. Process varies in 64-bit/other architectures.- See system_call interrupt handler and syscall dispatch under
/arch/x86/entry - See
sys_read()implementation in/fs/read_write.c:SYSCALL_DEFINE3(read, unsigned int, fd, char __user *, buf, size_t, count) { return ksys_read(fd, buf, count); }
System Call Parameters
Syscall parameters are passed via registers
- max arg size is register size
- use struct pointer to pass in more/larger arguments (e.g.
struct sigaction *)
Memory validation
We can’t let user programs trick the kernel using malicious addresses:
read()/write(): what ifbufactually points to kernel memory?
System calls must validate pointer parameters before copying:
// /include/linux/uaccess.h
static __always_inline unsigned long __must_check
copy_to_user(void __user *to, const void *from, unsigned long n);
static __always_inline unsigned long __must_check
copy_from_user(void *to, const void __user *from, unsigned long n);
Last updated: 2023-02-19